 Have You? (Best Practices)
Have You? (Best Practices)
By Gideon T. Rasmussen, CISSP, CRISC, CISA, CISM, CIPP
This is a collection of my HaveYou best practices posts. Most of the advice addresses cybersecurity beyond frameworks. Operational risk and professional development tips are also included.
Have you established annual goals for your InfoSec program? Many organizations begin the planning process in October. This post includes a brainstorming meeting, performance plans and an initiatives portfolio.
https://www.gideonrasmussen.com/annual-goals.html

Have you created a Program Welcome Packet? Include an executive summary, roles & responsibilities, a mid-level overview and a process diagram at the end.

Have you included Operations Security within your awareness program? Loose lips sink ships. 4 issues here: No privacy filter, Screen lock does not engage, Laptop left unattended & Employee is consuming alcohol while working (text has been blurred out within the image)

Have you evaluated critical business processes? There is risk as a process crosses swim lanes between functions. Process diagrams often depict business as usual. Have you planned for failure? Are quality assurance and fraud prevention controls in place? Conduct an assessment to ensure appropriate controls are in place to protect assets and service availability.
Have you hosted an InfoSec coffee break? Engage technologists and have meaningful conversations. Discussions about process and control improvements occur organically. Coffee break calls also result in cultural change, security advocacy and risk mitigation.
http://www.gideonrasmussen.com/infosec-coffee-break.html

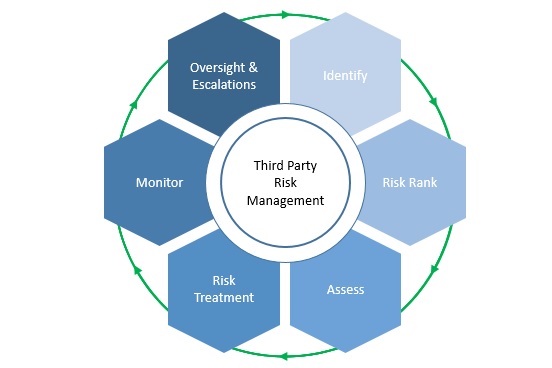
Have you established a Third Party Risk Management Program? Third party risk can be significant and vendor security posture varies. Third Party Risk Management has been elevated to a board-level concern.
Have you locked down Microsoft PowerShell in your IT environment? PowerShell is a tool used by Windows System Administrators. Adversaries leverage it because the software is already in place and installing malware increases the risk of detection.
Here are PowerShell hardening resources from Microsoft:
https://docs.microsoft.com/en-us/sccm/apps/deploy-use/learn-script-security
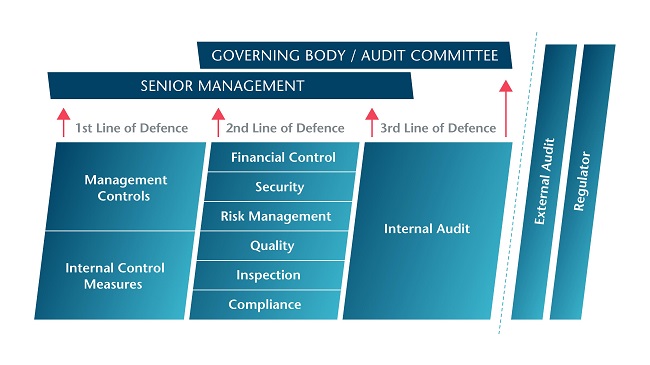
Have you considered three lines of defense for your Enterprise Risk Management Program? 1st: Operational Management, 2nd: Risk Management and Compliance, 3rd: Internal Audit
https://www.iia.org.uk/resources/audit-committees/governance-of-risk-three-lines-of-defence/
Have you updated your cybersecurity program to keep pace with changes in the threat landscape? Mitigate new data breach techniques and search for indicators of compromise.
http://fortune.com/2018/09/24/business-strategy-technology-mckinsey/
Have you established an Information Security Plan? The act of documenting your program requires deliberation, analysis and investigation. The gaps become obvious. You can can plan to address operational risk from there.

Have you created a Job Search Portfolio? Be proactive and drive your career forward. This page includes tips for creating a Resume with proof points, a Career Profile Slide and a Portfolio to pull it all together.
http://www.gideonrasmussen.com/job-search-portfolio.html

Have you audited your Access System for rogue ID badges? Compare badges to a list of current personnel. Review badge images for anomalies such as fictional characters (true story).

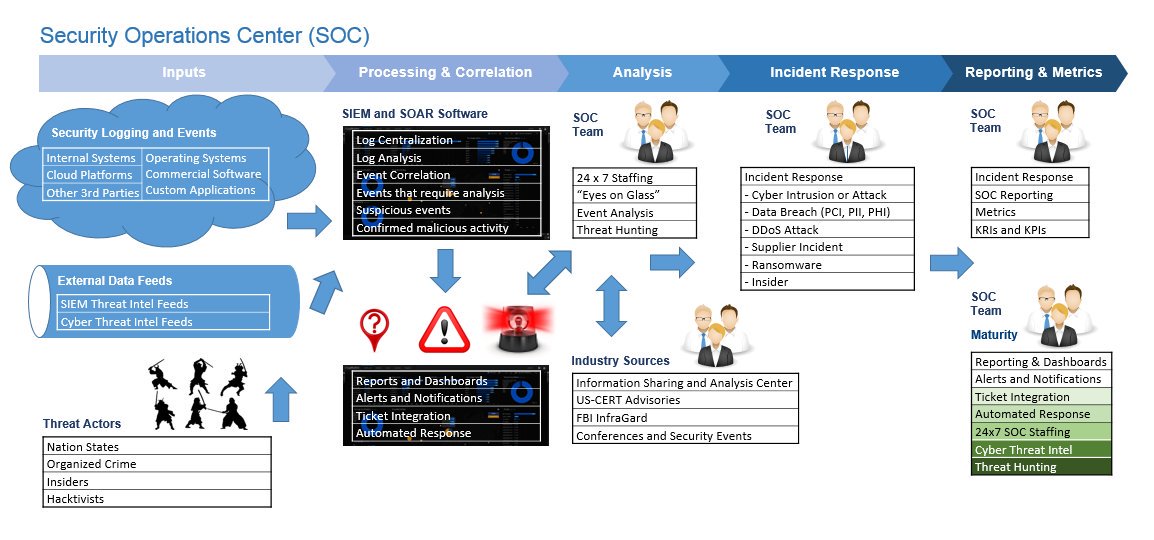
Have you implemented a SIEM and 24x7 security monitoring? Your adversaries reside in multiple time zones. It makes sense to have someone actively monitoring your systems, available to respond to suspicious activity.
Have you evaluated natural disaster risk at mission-critical facilities? Consider your headquarters and data centers. Reference the 'FEMA National Risk Index' for more information.
https://www.fema.gov/press-release/20201117/fema-publica-el-indice-nacional-de-riesgo-nuevos-datos-disponibles-en-linea
Have you conducted exercises within your organization recently? It's necessary to test your incident response, disaster recovery and business continuity plans. Each exercise scenario should include a significant disaster, such as loss of an office building. Otherwise, responding to an incident will be like facing off against another team without practicing before the season.
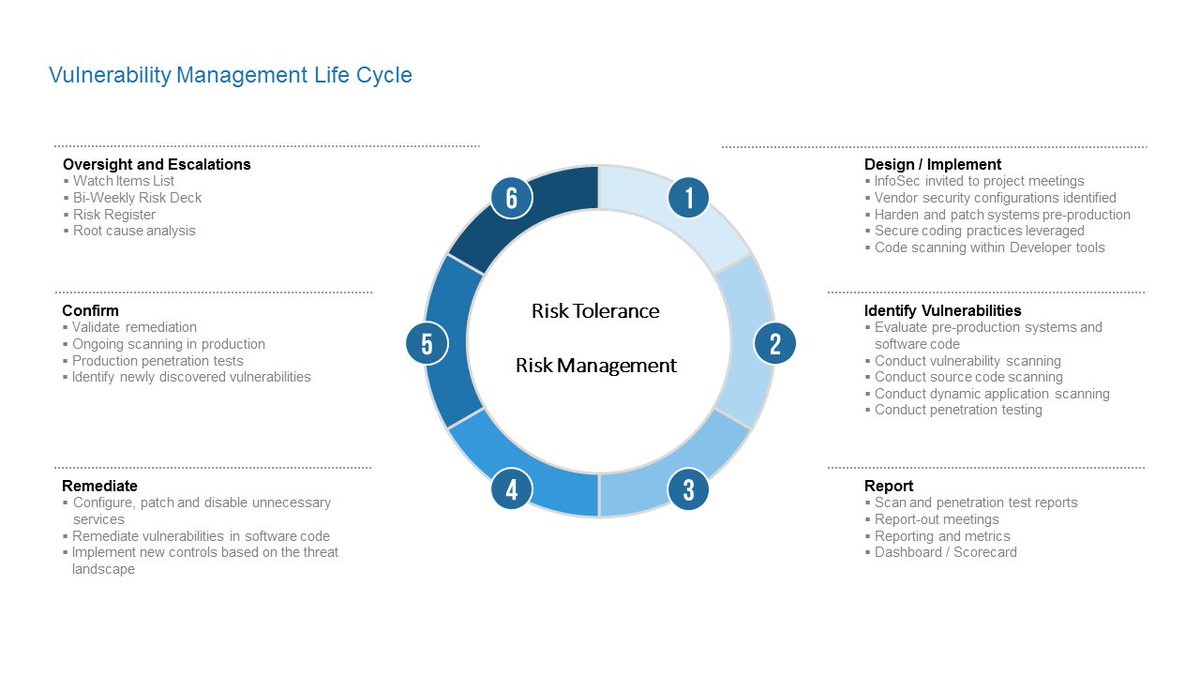
Have you established a Vulnerability Management Program? Design processes and technology to minimize vulnerabilities from the start. Identify issues that could lead to significant business impact. Address them early. Track remediation to closure. Identify root cause and prevent reoccurrence.
Have you enabled DMARC? Block unauthorized use of domains for sending e-mail. Configure in discovery mode first to learn who is sending e-mail from your domains. That prevents disabling a supplier from sending legitimate messages on your behalf.
https://dmarc.org
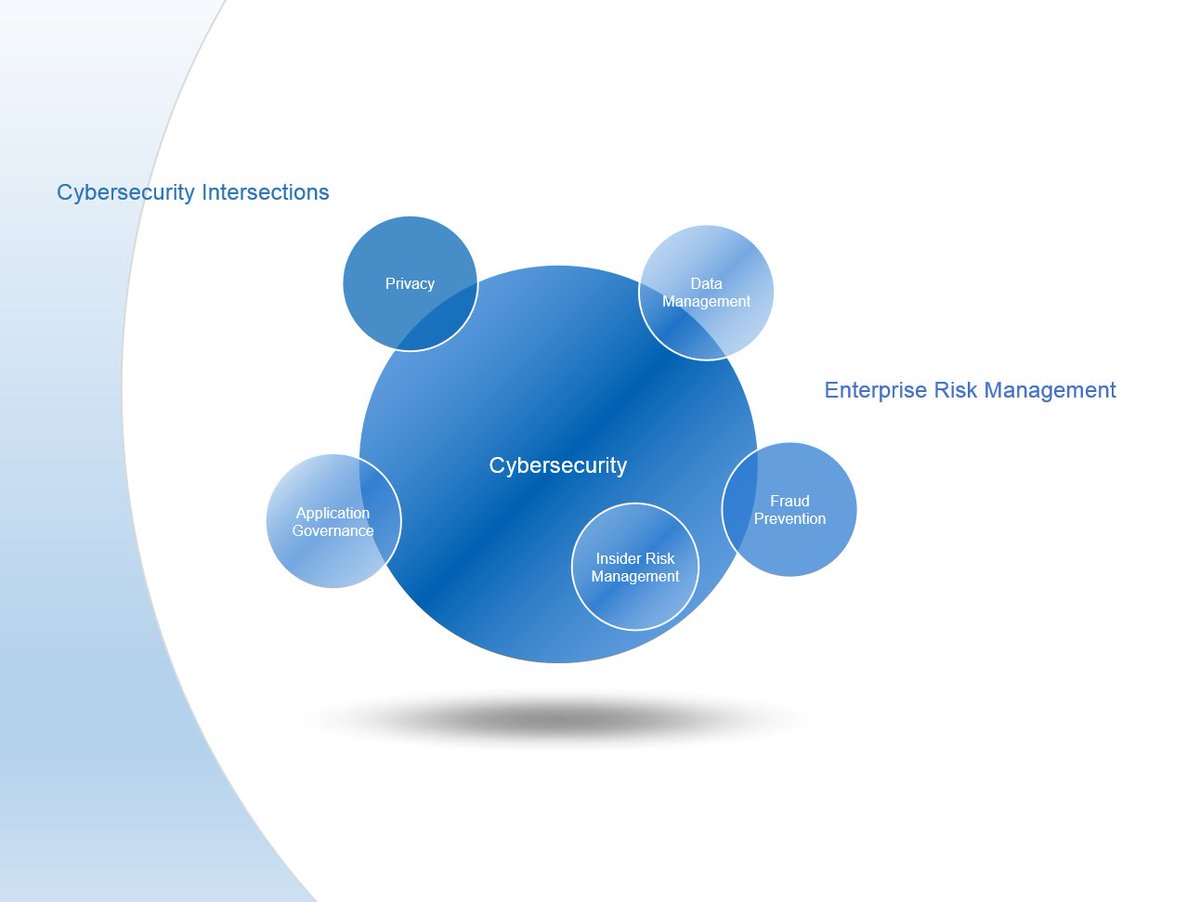
Have you established meeting routines with risk leaders? Cybersecurity intersects with several disciplines. Evaluate exposure and leverage existing processes to mitigate risk more effectively. It all comes down to Enterprise Risk Management.
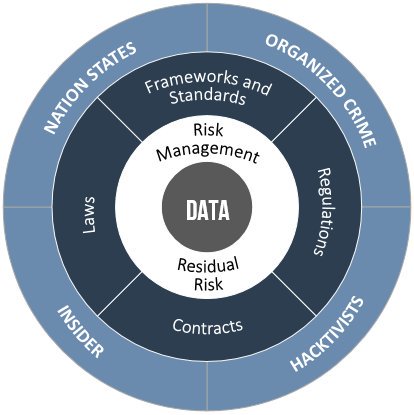
Have you conducted a risk assessment? Identify potential for business impact. Evaluate threat actors, attack techniques, in-place controls and vulnerabilities. Minimal compliance is a fail. Give me a call.
Have you implemented a process to track assessment findings to closure? Mitigate the risk or open a Risk Register entry. Require the appropriate tier of management to sign-off on risk acceptance based on the severity of the issue.
https://www.nextgov.com/cybersecurity/2018/07/nsa-hasnt-implemented-post-snowden-security-fixes-audit-finds/150067/
Have you conducted a war gaming exercise? Test incident response capabilities against a real world adversarial scenario. Include business leaders. Evaluate plan effectiveness, execution, decision making and communications. Reach out to me for details.

Have you refreshed your wardrobe? Invest in your career. Go to a Clothier. They can help design a unique style you are comfortable with. Patterns that stand out just a bit, colors that make you look forward to going out. Ties that pop!

Have you established a Program Governance Function? Confirm controls are effective. Use automation to detect and respond faster. Increase team capacity to implement new controls, reducing risk further. Reduce 'compliance jitter' and ensure controls remain in place between assessments.

Have you established a Threat Hunting function? It could mean the difference between a security incident and a data breach.

Have you taken a hard look at insider threat in your organization? Insider is one of the core threat actor categories. Contact me for an assessment proposal.

Have you applied vendor security configurations for commerial software and online services? Attackers download Admin Guides from the Internet.

Have you used Failure Mode and Effects Analysis to evaluate process and system controls?
https://www.gideonrasmussen.com/article-17.html
Have you established a risk register process? Influence risk mitigation and provide risk transparency to executive leadership.

Have you established a Crisis Communications Plan? Otherwise a News Anchor will riff about what 'may' have occurred.

Have you conducted an assessment of your InfoSec program? Contact me for an assessment customized to your needs.

Have you documented a Risk Management Strategy for your organization? That is a core component of a cybersecurity program.

Have you scheduled reoccurring meetings with your business partners? Understand the view from their side of the table. Establish a relationship before discussing an urgent need to address a security issue.

Have you established an Alternate Duties List? The Primary contact is responsible for day-to-day tasks associated with their process/function. The Primary develops procedures, training materials and other relevant documentation. The Alternate contact is responsible for completing on-the-job training, critically evaluating documentation and being fully prepared to perform the Primary's role.

Have you dedicated resources to detective controls? Setting a SIEM on auto-pilot is not sufficient. Invest in SOC personnel, process and procedures. Conduct threat hunting to actively search for adversaries within your IT environment.
https://www.scmagazine.com/home/security-news/data-breach/godaddy-takes-seven-months-to-discover-data-breach
Have you established metrics, KPIs and KRIs within your cybersecurity program? Take a proactive approach. "What cannot be measured cannot be managed". - W. Edwards Deming

Have you aligned your cloud computing implementation to a framework? Conduct a health check to ensure appropriate security tools and configurations are in place. Otherwise, track to closure in a POA&M or in a risk register.
Have you included social engineering within your cybersecurity program? Provide social engineering prevention tips within security awareness training. Establish detailed procedures for authenticating customers, employees and contractors. Once that is in place, test with a social engineering assessment.
https://gizmodo.com/attackers-dupe-godaddy-staff-into-helping-them-take-dow-1845733837
Have you included cybersecurity requirements within vendor contracts? This is an absolute must if you are sharing sensitive data. Strong contract language enables a Third Party Risk Management Program and incident response.
https://www.law.com/corpcounsel/2020/12/02/vendor-contracts-poised-to-become-work-of-art-as-cybersecurity-dangers-grow
Have you taken a hard look at privacy practices and tech in your organization? Consumers should never be surprised by how their data is used. The FTC is known for citing companies for unfair or deceptive practices. They issue significant fines and require up to 20 years of privacy assessments.
https://gizmodo.com/ftc-orders-amazon-youtube-discord-and-6-more-to-expl-1845881402"
Have you created a Performance Plan? Architect goals to gain experience. Increase your chances of receiving a healthy bonus. Prove yourself 'ready now' for promotion. Here are five steps to take control of your career:
https://www.gideonrasmussen.com/performance-plan.html

Have you considered the MITRE Shield Framework? It contains 27 detect/disrupt controls to mitigate adversary tactics, techniques and procedures (TTPs). This could be a logical next step once NIST Cybersecurity Framework controls are in place.
https://medium.com/mitre-shield/three-simple-ways-to-deploy-an-active-defense-with-mitre-shield-95ae639a50b5
Have you integrated quality assurance into critical business processes? QA is a method to evaluate whether controls are in place and effective. QA reviews are conducted in partnership with other teams and functions. The goal is to correct process execution issues before there is business impact. QA is a second line control function within ‘The Three Lines of Defense Model’ (IIA).

Have you confirmed monitoring for suspicious activity is in place? Review recent CISA advisories for approaches to uncover malicious cyber activity. Do not assume the SIEM will detect and alert based on default configurations. Test the effectiveness of each alert and the end-to-end security monitoring/response process (trust, but verify).
Have you conducted a physical security assessment? It's easy to overlook design flaws such as the Breakfast Club vulnerability. It's also important to evaluate exposure to physical breach tools and tactics.
https://www.theregister.com/2022/07/07/lock_down_your_piss_corridor

Have you requested an Intern to support your cybersecurity program? Give them a meaningful project. Provide on-the-job training and experience. Increase capacity to identify and mitigate risk. Establish a pipeline of entry-level cybersecurity talent.

Have you conducted health checks of critical systems and software? Evaluate security configurations and monitoring. Confirm security logs, events and alerts are replicated to monitoring software. Determine if appropriate alert configurations are in place.

Have you embraced process design? Produce consistent results and enable process risk assessment. Program architecture provides stability and the ability to focus on developing new services.
https://www.govtech.com/sponsored/how-process-mining-supports-the-push-for-digital-government-services
Have you established a comprehensive set of cybersecurity tools? Cybersecurity software is necessary to identify and mitigate risk in your organization. Cyber tools are also necessary for retention of cybersecurity professionals. They need the right set of tools to fulfill common tasks and activities just like in the physical world. Your organization's toolset must be kept current to address emerging threats and changes in technology. Fair warning...

Click here for more professional development tips
 Have You? (Best Practices)
Have You? (Best Practices)


































